
The Evolution of Security: From Simple Passwords to Layered Defense
The Evolution of Security: From Simple Passwords to Layered Defense
In the early days of security, a simple password or Personal Identification Number (PIN) was the primary mechanism for access control. This single-factor method offered basic individual authentication and accountability. However, as cyber threats became more sophisticated, this “one-key” system became a major liability.
Today, the industry has pivoted toward Multi-Factor Authentication (MFA), building layered defenses that are exponentially more secure.
Crucial Fact: Microsoft reports that MFA prevents over 99.9% of account compromise attacks, making it the essential baseline defense against modern threats.
The Password Problem: Why We Must Evolve
The concept of using a private, memorable code for access emerged to offer simple, cost-effective, and easy-to-deploy access control for early computing and security needs. The primary advantage of this system was its initial user-friendliness and extremely low initial cost and maintenance for rudimentary access.
However, the disadvantages of relying solely on a single password have grown severe, exposing organizations to catastrophic risks:
- Vulnerability to Brute-Force and Dictionary Attacks: Weak or common passwords are often compromised in a matter of seconds by automated tools.
- Susceptibility to Phishing and Social Engineering: Attackers are adept at tricking unsuspecting employees into willingly giving up their credentials.
- Password Reuse and Fatigue: Users frequently reuse the same credentials across multiple sensitive systems, meaning the compromise of one service jeopardizes everything else.
- Default and Weak Credentials: Many systems are deployed with easily guessable default passwords that are never changed.
This undeniable, documented vulnerability highlights the desperate need to move beyond single-factor authentication. The transition is not optional; it is crucial, because a staggering 49% of data breaches involve the use of stolen credentials, according to the 2023 Verizon Data Breach Investigations Report. This evidence proves that passwords alone are no longer a viable security solution for any business.
The solution is MFA, which requires a user to present two or more verification factors from different categories (something you know, something you have, or something you are) to gain access.
MFA in Action: Securing the Corporate Server Room
Multi-Factor Authentication is not just for logging into email; it is essential for physical access control where high-value assets are present.
Consider this Real-Life MFA Use Case: Securing a Corporate Office.
Imagine a modern tech firm’s headquarters where the main server room—housing intellectual property, critical data, and physical hardware—must be accessed by only authorized IT personnel. Instead of employees simply swiping a single, easily lost or stolen access card (something they have), the access control system implements a robust MFA sequence:
- Factor 1: Something You Have (Proximity Card): The employee initiates access by tapping their unique ID badge against the reader.
- Factor 2: Something You Know (PIN Code): The system then requires the employee to input a unique, private PIN on the keypad.
- Factor 3: Something You Are (Biometric Scan): Finally, the system demands a fingerprint scan (or facial recognition) for irrefutable verification.
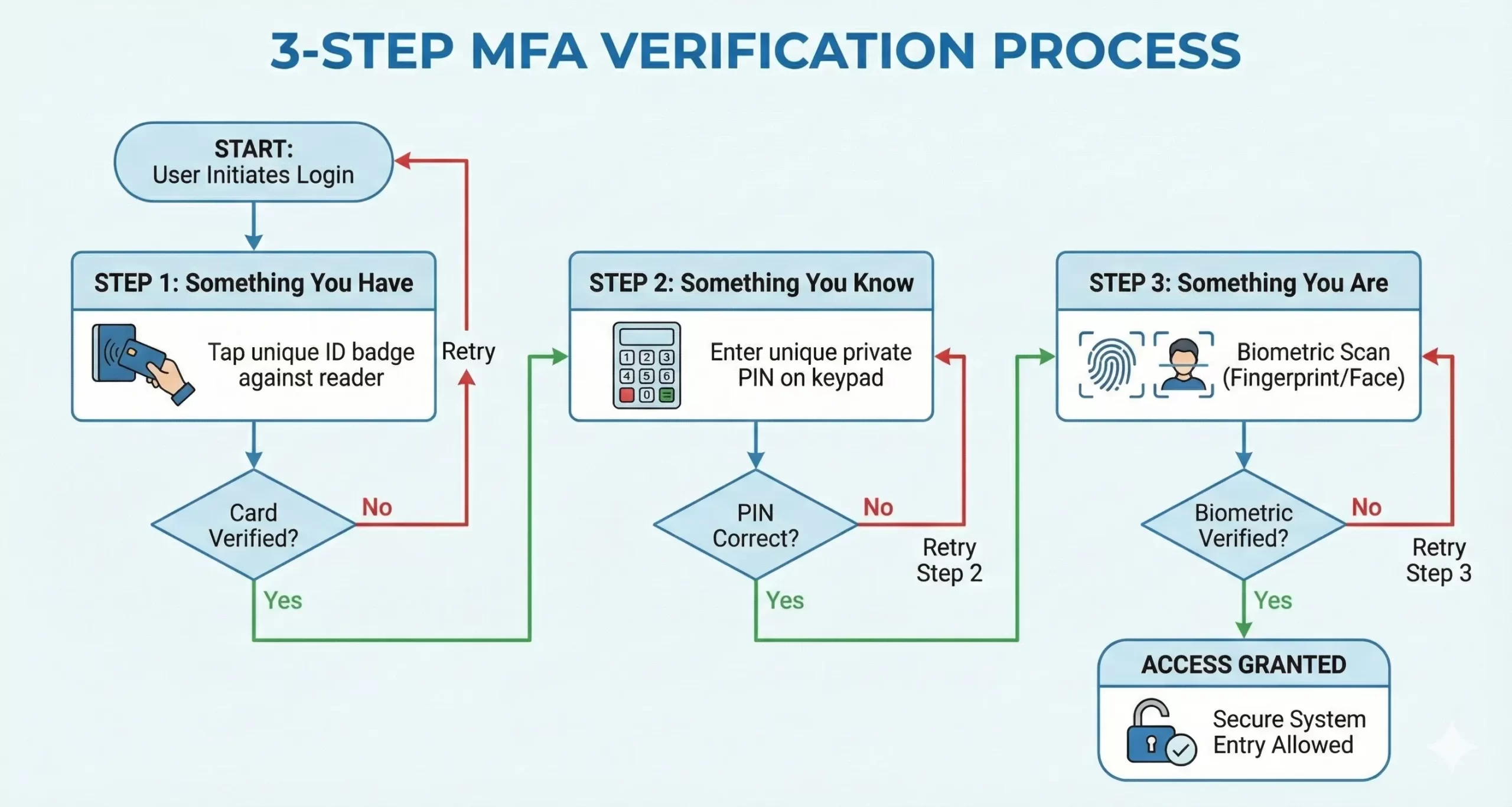
This robust, layered approach means that even if a thief successfully steals an employee’s access card and manages to guess their PIN, they still cannot enter the secure area without the legitimate employee’s unique biometric data.
Why Your Organization Needs MFA Now!
Implementing MFA creates an impenetrable perimeter and yields significant advantages for your organizational security posture:
- Significantly Increases Security: By demanding multiple, independent verification factors, MFA creates an exponentially higher barrier for unauthorized users to breach, making successful credential theft virtually useless.
- Mitigates Credential Theft Risk: Stolen or leaked passwords become useless to an attacker because they still lack the second, crucial factor (like the one-time code or biometric data).
- Ensures Regulatory Compliance: Many industry regulations and standards—such as the Health Insurance Portability and Accountability Act (HIPAA) in healthcare and the Payment Card Industry Data Security Standard (PCI-DSS) in finance—now mandate strong authentication, making MFA a legal necessity.
- Enhances Remote and Hybrid Workforce Security: As workforces become distributed, MFA ensures that employees securely access both physical premises and critical corporate resources from any approved location or device.
Leading the Way: MATRIX and the Essential Role of MFA in Access Control
The transition from single-factor to Multi-Factor Authentication is not merely an upgrade; it is a basic necessity for any organization operating in today’s threat landscape. Ignoring this security evolution is akin to leaving the most sensitive areas of your business unprotected.
This is where companies like MATRIX have positioned themselves at the forefront of access security. MATRIX access control solutions are designed with Multi-Credential Support and integrate the most advanced MFA techniques – including Biometrics (Fingerprint, Face, Iris), Card (RFID, Smart), and PIN – as a fundamental, configurable part of their offering.
By adopting a system that treats multi-factor authentication as the absolute baseline, your organization can move forward confidently, knowing your most sensitive data and physical premises are protected by an essential, layered defense against today’s sophisticated threats.

